Who We Are
Meet our core team
Derek Harp
Founder & Executive Chairman
Derek is a 27 year serial entrepreneur, co-founder, and advisor to 12+ start-ups. He has had 2 cybersecurity company exits. He is the co-founder of the SANS ICS Program & founding co-chair of the industry leading GICSP certification. He is also the founder of (CS)2AI, a 38,000+ member industry professional association 501c6 non profit.
Jonathan Pollet
Co-founder & Chief learning officer
Jonathan is a 25 year entrepreneur, Electrical Engineer, and one of the original thought leaders in the industry. He has written 125+ whitepapers and articles and has presented 200+ times at industry conferences. He helped create 8+ industry standards and was the first in the industry to design and deliver training to 4000+ people. He is the founder of Red Tiger Security.
Marty Edwards
Faculty Board Chair
Marty is a 30+ year industry pioneer. He was the former Deputy CTO for OT/IoT at Tenable and the 2022 Group Lead for the National Security Telecommunications Advisory Committee (NSTAC), reporting to the POTUS on IT/OT convergence. He testified regularly about ICS to the U.S. Congress and served as the Global Director of Education at the International Society of Automation (ISA). He is the longest serving Director of the US Department of Homeland Security Industrial Control Systems Cyber Emergency Response Team (ICS-CERT).
Trisha Harp
Co-founder & VP Marketing
Trisha is a 27 year serial entrepreneur, including 5+ start-ups. She is a 5 times published author, including a Best Selling author. She is also the co-founder of (CS)2AI, a 38,000+ member industry professional association 501c6 non profit.
Our mission is to provide customizable cybersecurity training to upskill your organization's entire workforce
What We Offer
Training
OT security training for your organization including optional integration with your LMS.
Competency Mapping
Service to work with your organization to map
required competencies and create training plans.
Co-Development
Co-development of training to meet your OT security training requirements and tailor training to your needs.
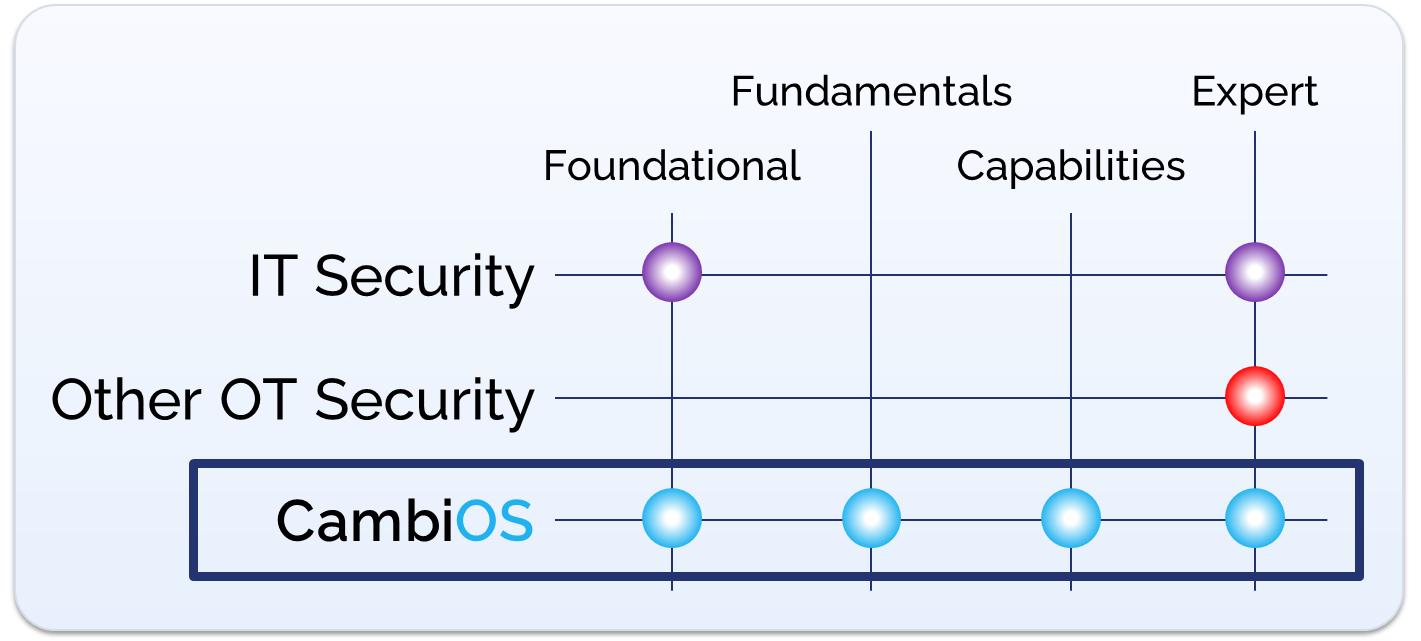
How We Do it: The CambiOS Process
02
Identification of Learning Aids
04
Validation of Instructional Content
Why Choose Us
Why Choose Us
Why Choose Us
Why Choose Us
Why Choose Us
Why Choose Us
Why Choose Us
- We are intimately familiar with the challenges organizations face and are driven to deliver training programs that meet your unique needs